Cloudflare offers API access to it’s WAF IP access rules, which can be a great tool to ban bots on a “edge” level, reducing load on each instance. So once a server bans an IP for repeatedly failing auth, it will be blocked on the CF level, unable to bother other servers.
My old script has stopped working, apparently Cloudflare have changed their APIs. Luckily there’s an official fail2ban action now, grab it directly from their Github: https://github.com/fail2ban/fail2ban/blob/master/config/action.d/cloudflare.conf
Add it to the actions.d folder, configure the cftoken und cfuser variables with your own global Cloudflare API token (My Profile -> API Tokens -> Global API Key)
[Init]
# If you like to use this action with mailing whois lines, you could use the composite action
# action_cf_mwl predefined in jail.conf, just define in your jail:
#
# action = %(action_cf_mwl)s
# # Your CF account e-mail
# cfemail =
# # Your CF API Key
# cfapikey =
cftoken = YOURGLOBALAPIKEY
cfuser = YOURCLOUDFLAREMAIL
cftarget = ipNow you just need to add the action to your jail configuration like this:
action = cloudflare
iptables-allportsI mainly use it for my repeatoffeners jail, which is set to monitor fail2ban logs and ban those who have been banned multiple times within the last 30 days, this can look like this:
[repeatoffender]
maxretry = 6
findtime = 2592000
bantime = 2592000
enabled = true
filter = repeatoffender
action = cloudflare
iptables-allports
logpath = /var/log/fail2ban.logNow let’s test the new setup, first a manual fail2ban ban:
fail2ban-client -vvv set repeatoffender banip 55.55.55.55Check the Tools tab in Cloudflare’s WAF setting to make sure it worked:
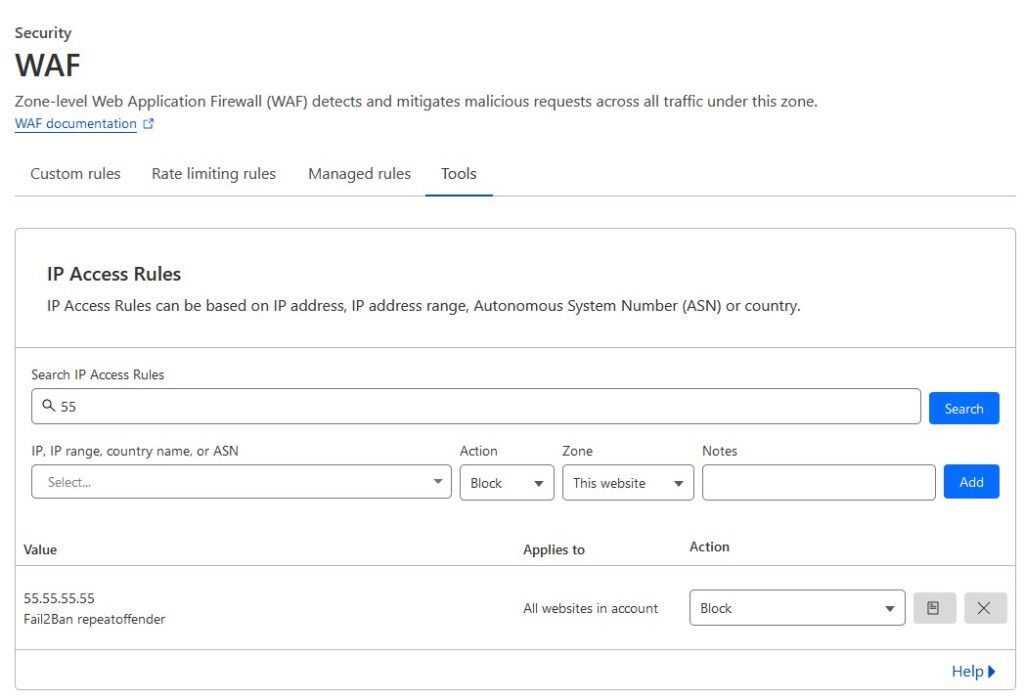
now test the unban command:
fail2ban-client set repeatoffender unbanip 55.55.55.55IP address should now disappear from Cloudflare IP Access Rules.