A Virtual Private Cloud (VPC) on AWS is an isolated network you create in the AWS cloud.When you create a VPC, you need to choose three main things. After you create your VPC, you need to create subnets inside of this network. Subnets are like virtual area networks (VLANs) in a traditional, on-premises network. In…
Tag: security
Set Cloudflare WAF rules with Fail2Ban actions
Cloudflare offers API access to it’s WAF IP access rules, which can be a great tool to ban bots on a “edge” level, reducing load on each instance. So once a server bans an IP for repeatedly failing auth, it will be blocked on the CF level, unable to bother other servers. My old script…
AWS IAM Policies & Roles
Policies are stored in AWS as JSON documents with several policy elements. When creating a policy, it is required to have each of the following elements inside a policy statement. Element Description Required Example Effect Specifies whether the statement results in an allow or an explicit deny ✔ “Effect”: “Deny” Action Describes the specific actions…
AWS Security Basics
AWS Shared Security Model: https://d1.awsstatic.com/security-center/Shared_Responsibility_Model_V2.59d1eccec334b366627e9295b304202faf7b899b.jpg AWS is responsible for security of the cloud. This means AWS is required to protect and secure the infrastructure that runs all the services offered in the AWS Cloud. AWS is responsible for: The level of responsibility AWS has depends on the service. You’re responsible for security in the cloud.…
Username Enumeration with ffuf
We can use the existence of error messages like “Sorry, that username already exists!” to produce a list of valid usernames already signed up on the system by using the ffuf tool below. The ffuf tool uses a list of commonly used usernames to check against for any matches. In the above example, the -w argument…
Get an Email notification for successful SSH logins
This is an email alert that is triggered once a SSH login succeeds First we will create the script itself in the ssh folder /etc/ssh/login-notify.sh: Make the file executable, then add the following line to the end of the sshd pam file in /etc/pam.d/sshd It’s set to optional for testing, as it would prevent login…
A script to secure the server using IPtables firewall
Use this bash script to automate the configuration of the iptables firewall and persist rules over restarts.
How to secure the SSH Server on Ubuntu
This is a short overview of how to secure the SSH server on a fresh Linux system. We will cover the basics of setting up a robust SSH configuration to access and manage the remote machine later on. Secure the SSH Daemon Configuration File All the configuration of the SSH server we need to adjust…
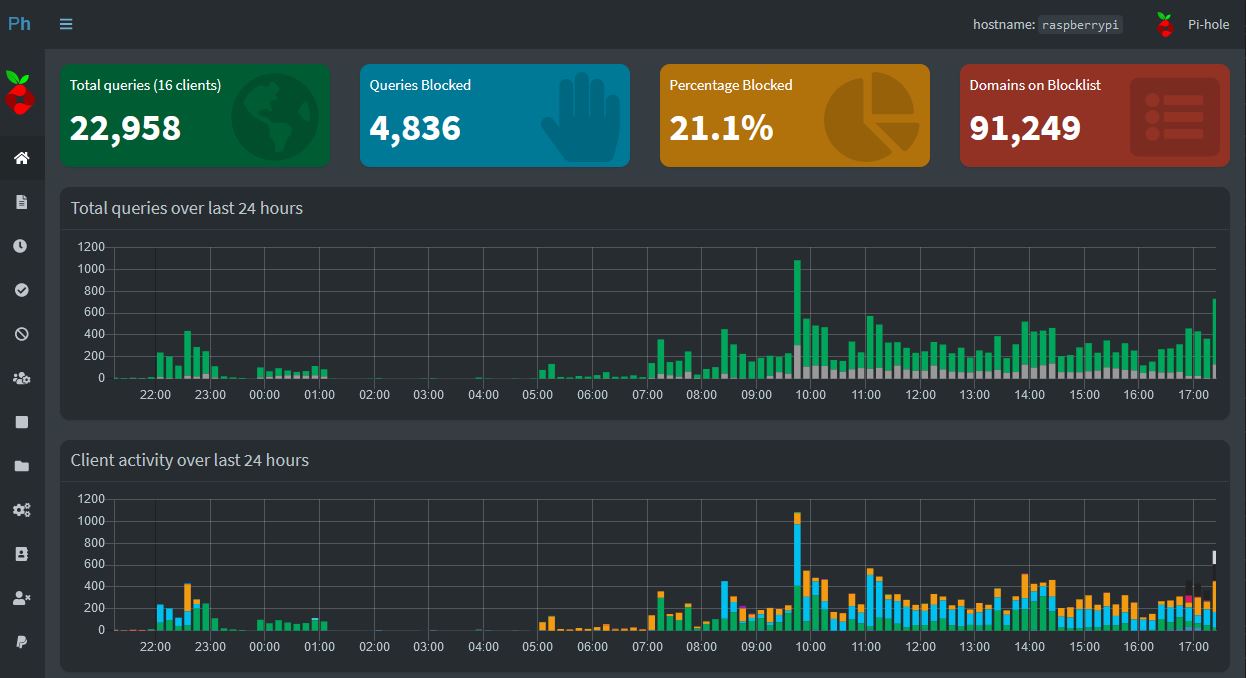
Pi-Hole on Raspberry Pi
The internet has always been invested with a lot of Ads, but the amount of tracking, personalized and intrusive Ads has grown exponentially. While I’ve kept my own devices setup to combat them, the number of smart devices and also users is growing at home. In addition, blocking the ads from displaying or the scripts…